Why you should implement Application Control within your business

In today’s digital world, businesses of all sizes are increasingly reliant on software applications to streamline their operations, enhance productivity and interact with customers. This dependence on so many applications, however, also exposes organisations to various Cyber Security risks.
To help mitigate these risks, a powerful tool to protect businesses from cyber threats is application control. This provides direct control over the applications running on an organisation’s networks.
What is Application Control?
Application Control is only allowing approved applications to run on systems to prevent malicious software from running. Unlike traditional antivirus software which focuses on identifying and blocking malware, application control software takes a proactive approach by explicitly only allowing authorised applications to run. By enforcing strict control policies, this software ensures that only approved applications can be executed, reducing the possibility of attacks and minimising the risk of unauthorised access, data breaches and malware infections.
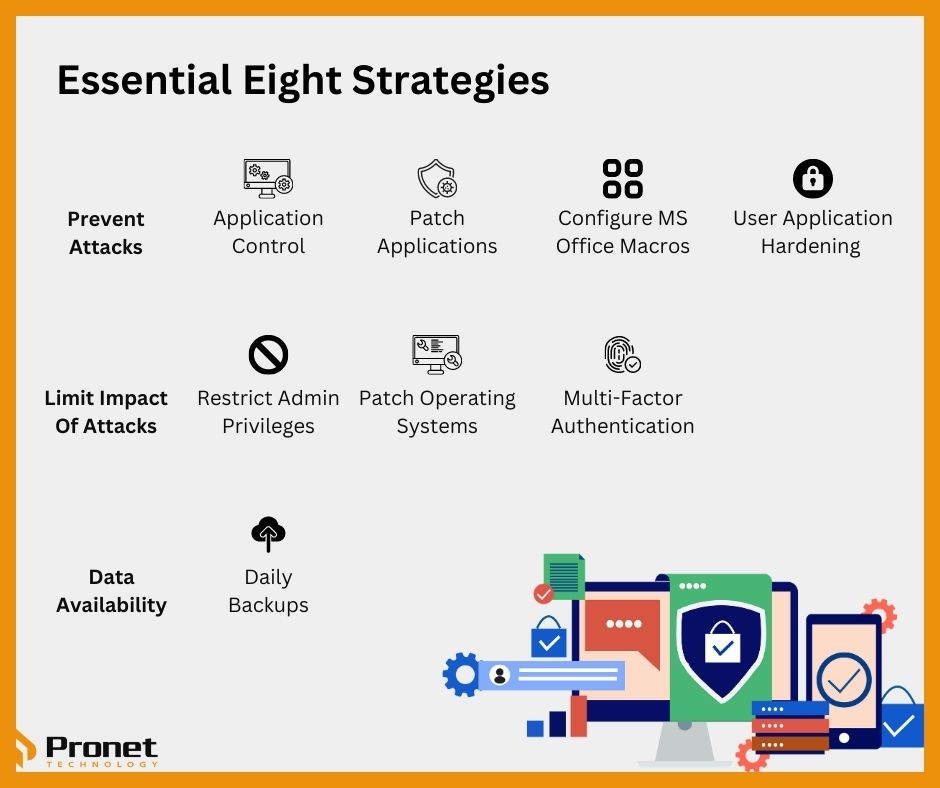
Essential Eight is a list of eight security strategies that the Australian Cyber Security Centre (ACSC) believes will provide a strong foundation for Cyber Security, and the framework is highly recommended by the government for businesses to implement. The first measure listed in Essential Eight is application control, showing just how effective it can be in protecting your business from cyberattacks. Keep in mind, though, that application control should not be the only Essential Eight strategy your business implements, and along those lines, Essential Eight should not be used in isolation to protect your organisation.
Key Benefits for Businesses
Preventing Unauthorised Software
One of the primary advantages of application control is its ability to prevent unauthorised software from being installed and used. By creating whitelists of approved applications, businesses can restrict employees from running potentially harmful or unverified software. This proactive approach reduced the risk of introducing malware or malicious code into the network, safeguarding sensitive data and intellectual property.
Minimising Vulnerabilities
Cybercriminals often exploit vulnerabilities in outdated or unpatched applications to gain unauthorised access to systems. Application control software can help businesses by monitoring and managing application versions and updates. By ensuring that all applications are up to date, businesses can reduce the likelihood of successful attacks through known vulnerabilities.
Enhancing Compliance
In highly regulated industries, like finance and healthcare, compliance with industry standards and data protection regulation is critical. Application control helps businesses meet these requirements by enforcing security policies and restricting the use of non-compliant applications. By maintaining a secure and compliant software environment, organisations can avoid hefty fines, legal implications and reputational damage.
Streamlining Incident Response
In the event of a security incident or breach, application control plays a vital role in incident response. By controlling the software environment, organisations can quickly identify and isolate compromised applications, limiting the impact of the incident and preventing its movement within the network. The ability to enforce restrictions and block unauthorised applications aids in containing the breach and restoring normal operations promptly.

Challenges of Implementing Application Control
While application control software offers several benefits for enhancing Cyber Security, there are some potential inconveniences associated with its implementation. It is important to consider these factors to ensure that businesses can strike a balance between security and operational efficiency.
Administrative Burden: Implementing application control software requires significant effort and ongoing maintenance. Creating and managing whitelists of approved applications can be time-consuming, especially for large organisations with a wide range of software dependencies. Regular updates and adjustments to application control policies may also require extensive coordination among IT teams and various business departments.
Compatibility and Integration Challenges: The software used for application control must be compatible with the diverse range of applications used within an organisation. Ensuring seamless integration with existing systems and workflows can be complex, particularly when dealing with legacy applications or custom-built software. Compatibility issues may require additional configuration or customisation, leading to delays and potential disruptions.
False Positives and False Negatives: Application control software relies on accurate identification and classification of applications to determine their status (allowed or blocked). However, false positives (legitimate applications mistakenly identified as unauthorised) and false negatives (potentially malicious applications not identified) can occur. False positives can disrupt operations, while false negatives may lead to security breaches. Regular monitoring and fine-tuning of application control policies are necessary to minimise these issues.
User Experience and Productivity Impact: Overly restrictive application control policies can result in reduced user productivity and frustration. If legitimate applications are mistakenly blocked or unauthorised applications are allowed to run, employees may encounter obstacles in performing their tasks efficiently. Striking a balance between security controls and user experience is crucial to maintain productivity while ensuring a secure security posture.
Impact on Innovation and Flexibility: Application control may sometimes get in the way of trialling new or emerging technologies within an organisation. Strict control policies may limit the ability to experiment with new applications or tools, potentially hindering innovation and agility.
Increased Dependency on Updates and Patching: Application control software relies on accurate information about application versions and updates to maintain security. Businesses need to stay vigilant in ensuring that they promptly apply patches and updates to both the application control software itself and the applications it monitors. Not doing this can introduce vulnerabilities or can prevent the control measures from functioning properly.

Sandboxing
One of the biggest concerns with application control is the need to test any updates or new applications through what is called, sandboxing, before it can be installed on the organisation’s systems. This generally takes about 24 to 48 hours, but you might find that some enterprise organisations, like banks, sandbox for up to a month to test for any threats before verifying the application.
Sandboxing each new application and update before using them in a business environment, while inconvenient for both staff and your managed service provider that needs to do this, is a critical practice that offers several benefits in terms of security, stability and risk mitigation.
Security Testing: Sandboxing allows you to test applications and updates in a controlled environment before installing them on your production systems. By isolating the software in a sandbox, you can observe its behaviour for potential security risks without putting your network and sensitive data at immediate risk. This helps identify and mitigate any vulnerabilities, malware or malicious activities associated with the application or update.
Risk Mitigation: Applications and updates can introduce unforeseen issues or conflicts with existing software or configurations. By sandboxing, you can assess the impact of these changes without jeopardising the stability and performance of your systems. Sandboxing enables you to identify and resolve compatibility issues, system conflicts or unexpected behaviour before implementing the software.
Protection against Malware: Malicious software, such as viruses, ransomware or Trojans, can infiltrate your network through compromised applications or updates. By sandboxing, you can run these potentially malicious software packages in an isolated environment, preventing them from infecting your actual systems.
Testing Application Performance: Sandboxing allows you to assess the performance and resource requirements of applications and updates. By monitoring their behaviour in an isolated environment, you can determine the impact on system resources, such as CPU, memory or disk usage. This evaluation helps you understand the application’s performance characteristics and ensure that it meets your business requirements without negatively impacting your production systems.
Compliance and Regulatory Requirements: Many industries have specific compliance and regulatory requirements that require thorough testing and validation of applications and updates. By sandboxing and evaluating software in a controlled environment, you can ensure that it meets the necessary security and compliance standards before introducing it into your production systems. This helps maintain data privacy, protect sensitive information and adhere to industry regulations.

What is ThreatLocker?
At Pronet, a software we implement within our clients’ systems to whitelist applications is ThreatLocker. It offers advanced features and capabilities to help organisations effectively manage and control the applications running on their networks. As a base, it employs a strong application whitelisting approach, allowing businesses to create a list of approved applications.
It also follows a zero-trust security model, meaning that it treats all applications as potentially untrusted until they are explicitly approved. This approach enhances security by ensuring that every application is thoroughly evaluated and authorised before execution, mitigating the risk of introducing malicious or unauthorised software.
ThreatLocker provides granular control over how applications interact with other areas of your IT systems, such as networks, files, folders and registries. This level of control allows businesses to fine-tune their security policies based on specific requirements. It allows organisations to enforce different access permissions and restrictions for different user groups or departments, enhancing security without impacting productivity.
The software also offers comprehensive reporting and auditing capabilities, providing visibility into application usage and security events. It allows businesses to generate detailed reports on application activities, policy violations and security incidents. ThreatLocker can integrate with other security solutions, such as antivirus software, firewalls and intrusion detection systems, to provide a layered defence strategy. This integration enables organisations to leverage multiple security measures and strengthen their overall Cyber Security framework.
Since ThreatLocker is a software Pronet uses, we know just how powerful it is and therefore, can recommend it.
In an era where cyber threats are a constant concern, businesses must prioritise Cyber Security measures to protect their assets, data and reputation. Application control software serves as a critical component in the overall Cyber Security strategy of businesses by allowing direct control over the software applications running on the network. By preventing unauthorised or potentially malicious applications from running, businesses can significantly reduce the risk of cyberattacks, data breaches and operational disruptions.