
Among all the components that a business needs to operate successfully, cybersecurity has now become one of those essential components. In the wake of COVID outbreak, businesses have stepped up their digital adoption, and threat actors are ready to grab the moment by going after companies of all sizes and industries. The year 2021 will go down in history as one of the most successful in terms of both security breaches and cyberattacks.
No matter what industry you’re in, attackers have no limits on what they may do. They just care about the data they can get their hands on and the money they can get for it. Even now, the attacks are getting more aggressive and smarter. If you are an employee of the company, then you must understand that you are on the front line of information security. Therefore, it’s important to stay on guard to help assure your company’s data is safe and secure. This article will focus on the best practices that employees should try to follow as human factors remains the primary reason for most of the cyberattacks happening in the world. Silly mistakes can bring devastating results and even complete closure of businesses in many cases. So, it is the duty of the employer and the employee too to be aware of cybersafe practices and follow them to remain safe. Let us start with these quick things:

Never Use the Company Email Outside of Work
For the sake of having all the updates in one single email, it is commonly seen that people use their work email for personal use, like for shopping, dining, etc. While it makes life easier, it’s also one of the riskiest things a person can do. Doing so unintentionally can put a business or corporation at risk. Your email can reveal confidential information about your company, which could cause the business to fail.
For instance, Australia’s one of the big universities, i.e., Deakin University was also a victim of cyberattack recently when an attacker used a staff member’s username and password to access student information via one of Deakin’s third-party providers. So, if you’re going to use your business email for personal purposes, think again about it.
Mind Your Clicks
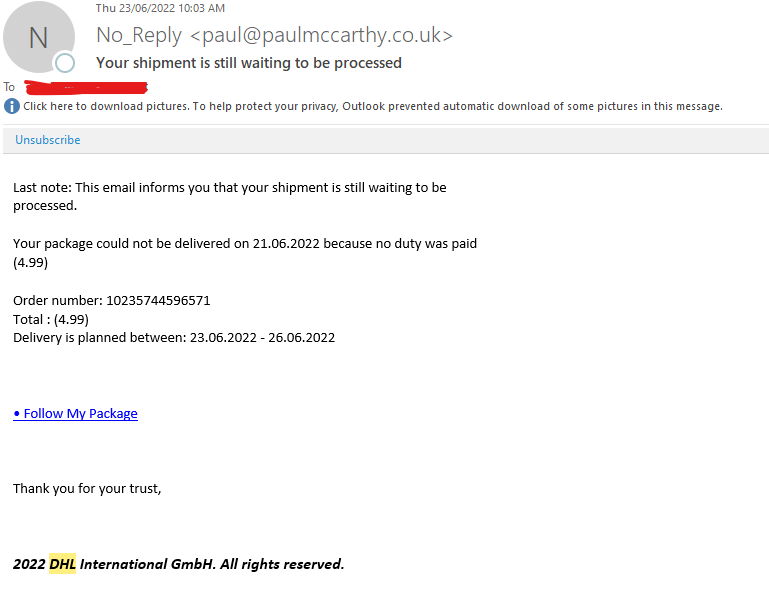
It is human nature to click on pop-ups, links, and ads if we personally receive them to know what value they offer. And, hackers savagely target this weak point of humans, and just with one click, they get access to your company data in a matter of seconds. These can be delivery emails pretending to be from DHL or Amazon, amazing offers, and so on, all designed to entice the reader to click the link. So, if you ever get an email with a link in it that doesn’t pertain to you, I suggest avoiding forwarding or clicking on it, and only notifying your company’s security staff. This would allow your company to put a halt to the attack and prevent it from spreading further at the time it occurs.
For instance, this is the phishing email we received a few days ago where the hacker portrayed himself as the shipment company DHL, but our employees are well-educated about the cyber safe practices and no one clicked on the link. The catch here was that the email i.d. that was used to send did not belong to the DHL company and all our employees realised the same.
Educate Yourself About Phishing Scams
Phishing scams are the most common scams that result in a security breach. Hackers or phishers lure employees to click on links that ask you to enter personal or company information, and once the information is entered, the whole network of the business is exposed to the hackers. It is very crucial to understand the difference between a genuine link and a corrupted one. If you are unsure of the link or email you have received to fill in the details, I suggest you immediately consult your I.T. department to verify. This will help prevent any cyberattacks.
Use Strong Passwords
So, again, to make our lives easy, we all use the same passwords or common passwords at work and in our personal lives. It simplifies our lives and even the lives of hackers too. Keeping common passwords gives an open invitation for hackers to compromise all the accounts using that password and, through them, give access to your company’s or business data. The last thing anyone would want is to be held responsible for such a devastating setback for a firm. So, just be mindful when creating passwords for the tools and software you use at work.
Never Share Passwords
So, another human trait is to have passwords written somewhere or to share them with someone trustworthy (according to you), which is not at all a good practice. Being humans, you never know when a person’s intention changes and it might be too late before that person misuses the information you have shared. It is a good practice for both personal and professional life not to share passwords with anyone.
Use 2FA While Logging into Devices, Software, etc.
An extremely safe option to use for staying safe in the present unsafe digital environment. You can try using different apps to have the authentication turned on for all of the logins. This will keep everything safe and even alert you instantly when there is an attempt to hack the accounts.
Make Sure all the Updates are Followed
Another thing that most of us ignore is the pop-up messages that come on our screen to update certain software, applications, etc. Usually, we all ignore or delay updating the installed software or applications, and this opens the gate for hackers to compromise the system from your machine, using your identity passwords, and have access to all your company’s sensitive data. If your company sends out instructions for any security updates, it is wise to install them all right away. Cyberthreats often take aim at your data. I am sure no one would want to be the reason for a cyberattack at their workplace, so next time when you see the update message on your screen, take the necessary action immediately.
Talk to Your I.T. Department
It is a good idea to learn more about the best practices to follow to be safe from cyberattacks online without any hesitation. Your I.T. department or I.T. partners will always advise you the best when it comes to cybersecurity. Reaching out to the I.T. department or person to alert them of any possible warnings is also advised to keep away any threats.
Use the Latest & Relevant Technology
Another major thing to keep in mind is to use the latest versions of tools, software, and technology in the workplace. If the licence of the software, applications, etc. you are using has expired or needs an update, do take the necessary action immediately as these outdated versions are most commonly used by hackers to attack. It is usually the duty of the I.T. department or external I.T. partner to suggest the best technology, but the employees should also be aware of putting forward any demand or need they have when it comes to technology they are using.
You Can Avoid a Data Breach
Having the right knowledge about how to identify spoofed content, links, emails, etc. is very crucial for strengthening your company’s defence against cyberattacks. Always remember: one corrupt click by you could let in a hacker and a single delay or failure to fix a flaw in time could become the primary reason for a cyberattack. So, take it as a part of your job to engage in safe online behaviour.
IT should be the backbone of every business and to help businesses leverage the same, Pronet Technology has been offering the best IT solutions along with cybersecurity tailored to your business needs and budget for more than 25 years now.
CALL US today at 03 9069 2188 to get a free consultation for your business IT requirements.
Stay tuned to our blogs to know interesting IT-related tips and facts.
References:
Graham, J. and Carey, A., 2022. Deakin University cyberattack: Hackers get details for 47,000 current and former students. [online] Theage.com.au. Available at: <https://www.theage.com.au/national/victoria/hackers-get-details-of-47-000-current-former-students-in-deakin-uni-cyberattack-20220713-p5b16v.html?fbclid=IwAR23ya2lPoU0L7_ZxQhFipMEtbQLzlS8hw0sbhU3OuYtiKYriSNnBJps3w4> [Accessed 24 July 2022].
2018. Silver Magic Keyboard. [image] Available at: <https://www.pexels.com/photo/silver-magic-keyboard-1109543/> [Accessed 25 July 2022].
Cybint. 2020. 15 Alarming Cyber Security Facts and Stats. [online] Available at: <https://www.cybintsolutions.com/cyber-security-facts-stats/> [Accessed 24 July 2022].



