Which Essential Eight maturity level should my business be at?
You know what Essential Eight is and that the Australian Government highly recommends implementing it, but does that mean your business must be at the highest maturity level?

As cyberattacks continue to rise in frequency and sophistication, businesses of all sizes must take proactive steps to protect their sensitive information and assets. Australian Cyber Security Centre (ACSC) has developed the Essential Eight, a set of mitigation strategies that businesses can implement to significantly reduce the risk of a successful cyberattack.
The ACSC has defined four maturity levels to help organisations identify where exactly they’re at when it comes to their Cyber Security. These maturity levels aim to help businesses implement Essential Eight, originally introduced in 2017 and updated in 2023 after the increase in cyberattacks on Australian organisations. However, many business owners may wonder which maturity level they should be at when implementing the Essential Eight.
What are the maturity levels?
Maturity Level Zero: Indicates that your business has significant weaknesses in its overall Cyber Security and would be easy to exploit by attackers. If you’re at this level, any potentially confidential data or the availability of your systems and data are at risk of being compromised.
Maturity Level One: Organisations sitting in this level have some sort of processes to protect themselves from opportunistic attackers looking to infiltrate the masses, rather than individual businesses.
Maturity Level Two: These businesses have reasonable defences in place to defend themselves against cybercriminals specifically targeting their organisation. Criminals attacking these businesses are happy to invest more time and effort into bypassing security controls, such as by using targeted social engineering techniques when using phishing, but are also wary of spending too much time and money trying to compromise their victims. Businesses at this level introduce shorter timelines for action, ensure high-risk activities are logged and start thinking more broadly about potential threats.
Maturity Level Three: This is the highest level a business can be at where businesses are actively mitigating threats from adversaries that are constantly adapting their techniques and who are very focused on targeting specific, high-value organisations. These adversaries exploit any opportunities in weaknesses in the Cyber Security of the organisation and are willing to invest time and effort into understanding the organisation, their security control and their staff to gain access and evade detection.

What maturity level should my business be at?
Businesses start off being at level zero, but it’s time to understand that this must be changed and you need to increase the Cyber Security strategies in your business.
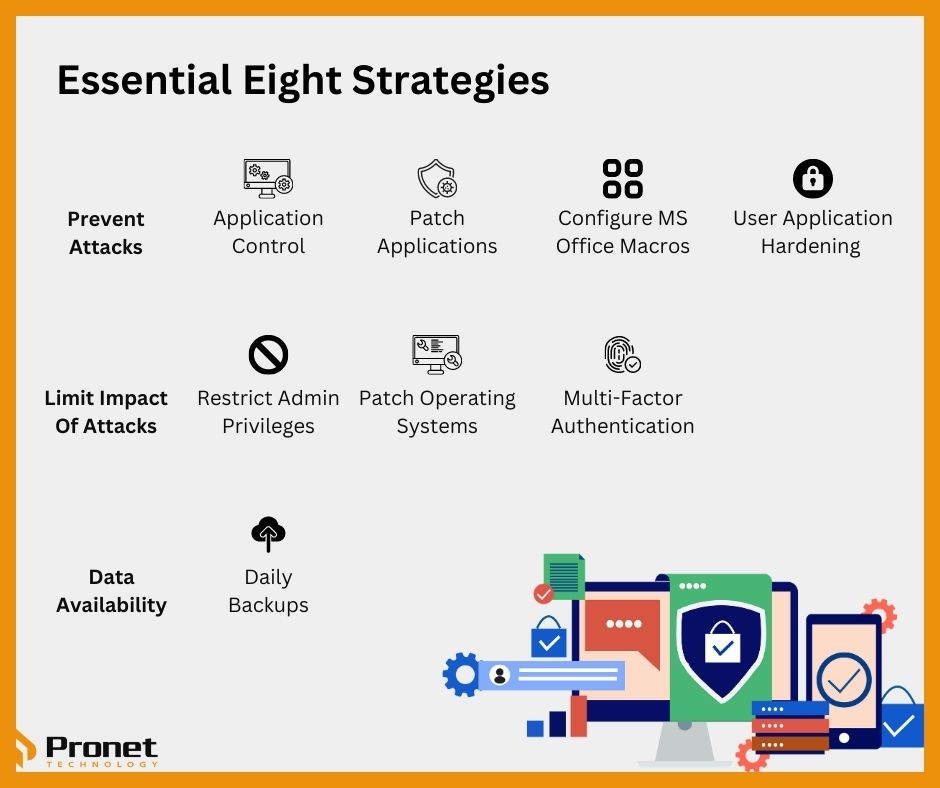
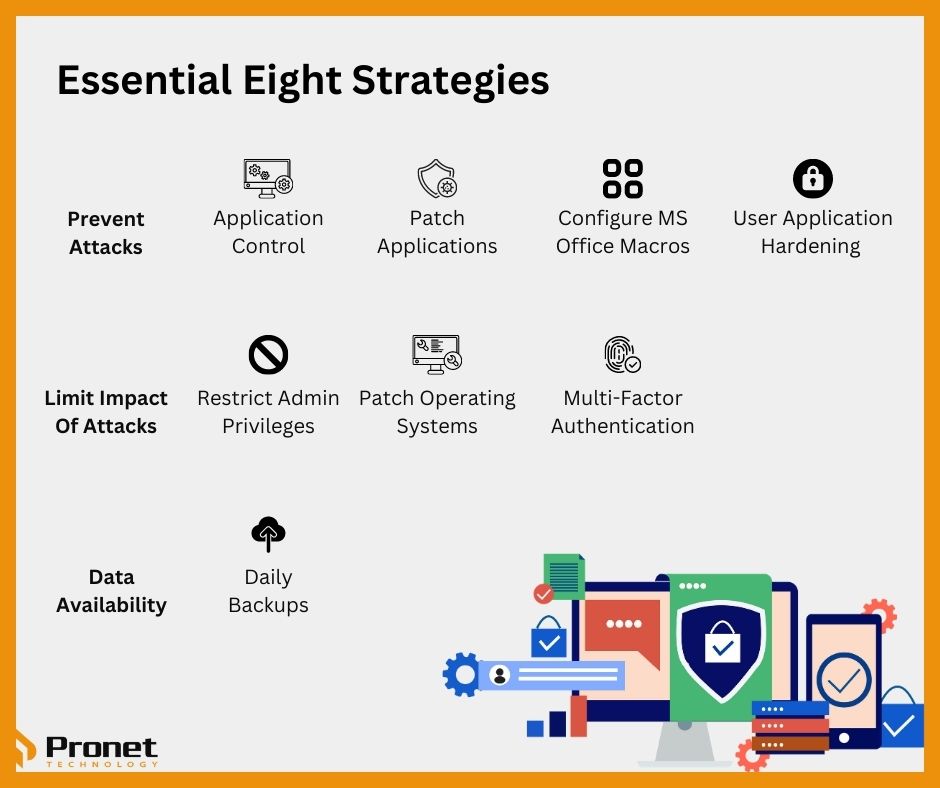
The first four of the Essential Eight strategies, known as the baseline maturity level, are considered to be the minimum requirement for all businesses. The remaining four strategies are part of the advanced maturity level and offer additional protection against cyber threats.
While implementing Essential Eight can help significantly reduce your risk of a cyberattack, it’s important to remember that it’s not a one-size-fits-all solution. Your business may require additional mitigation strategies beyond Essential Eight, and your business must conduct a comprehensive risk assessment to identify any gaps in your security. That is the first step in implementing Essential Eight. Focus on achieving a maturity level that makes sense for your business as the nature of your data might not be as sensitive as another business’ and Maturity Level Three might not correlate to your risk management evaluation.
So, which maturity level should your business be at? It ultimately depends on the size and complexity of your business, as well as the level of risk you are willing to tolerate. However, the baseline maturity level should be the starting point for all businesses, regardless of size or industry.
The baseline strategies include:
- Application control: This involves only allowing approved applications to run on your systems, which can help prevent malware and other malicious software from executing.
- Patching applications: Regularly updating applications with the latest security patches can help prevent cyber attackers from exploiting vulnerabilities in your systems.
- Patching operating systems: Like patching applications, regularly updating your operating systems with the latest security patches can help prevent cyber attackers from exploiting vulnerabilities.
- Restricting administrative privileges: Limiting the number of people who have administrative access to your systems can help reduce the risk of a successful cyberattack.
- Configure Microsoft Office macro settings: Cybercriminals often use Microsoft Office macros to deliver malware, so configuring the macro settings in Microsoft Office can help your business prevent this type of attack.
Once this level has been achieved, for businesses with higher risk levels, implementing the advanced maturity level strategies can provide additional protection. These strategies include:
- Multi-factor authentication: Requiring more than one form of authentication, such as a password and a security token, can help prevent unauthorised access to your systems.
- User application hardening: Configuring user applications to prevent malicious content from executing can help reduce the risk of a successful cyberattack.
- Daily backups: Regularly backing up your data can help ensure that you can recover quickly in the event of a successful cyberattack.
- Incident response: Developing and implementing an incident response plan can help minimise the impact of a successful cyberattack on your business.
Each mitigation strategy needs to be lifted to a higher level until the target maturity level is achieved as your business’ overall maturity is based on the lowest score of any of the strategies. This will not change unless all eight mitigation strategies are lifted to the specific target level. In the original iteration of Essential Eight, it aimed for all organisations to reach Maturity Level Three, but with the latest release, it aims for organisations to reach a homogenous maturity level across the strategies before then moving up to the next level.
Improving your business’ Cyber Security strategies can be an expensive process and achieving any maturity level of the Essential Eight strategies requires time. Start with the baseline, then work your way up to help reduce the costs in the beginning. While it can be a slow process, your business must ensure it’s beginning to improve its maturity level as cyberattacks become increasingly common, especially so among small to medium-sized businesses. What’s more, there’s a high chance that Essential Eight will be mandated in the near future for some, if not all, industries due to just how common these cyberattacks are occurring.
In summary, all businesses should start with the baseline maturity level of Essential Eight, regardless of size or industry. From there, businesses with higher risk levels may need to implement advanced maturity-level strategies for additional protection. It’s important to conduct a comprehensive risk assessment to identify any additional mitigation strategies that may be necessary for your business.