Essential Eight and why your business needs to Integrate Cyber Security

In today’s world, IT systems are an essential part of any organisation. They help in improving efficiency, communication and productivity. However, with the increasing use of technology, the risks associated with IT systems have also increased.
You must know what Essential Eight is if you’re an Australian organisation. It’s a cyber self-assessment security maturity tool to help organisations reduce Cyber Security incidents caused by cyber threats
The government currently recommends that organisations implement the eight essential mitigations as a baseline but we believe this will change in the future to be mandated so it is something we advise our clients and prospects to implement.
Developed by the Australian Cyber Security Centre (ACSC) to protect Microsoft Windows-based internet-connected networks, the framework has four maturity levels for each business’ risk category.
- Level Zero: not aligned with strategic objectives.
- Level One: partially aligned with the objectives.
- Level Two: mostly aligned with the mitigation strategy objectives.
- Level Three: fully aligned with objectives.
The levels depend on your business’ risk status and data sensitivity. Level One businesses, for example, are not commonly targeted specifically, so they just receive the typical mass scam emails. Level Two has the potential to be targeted but criminals will often move on if they find the security systems to be too hard to breach. Level Three are where attackers primarily focus as they have high dollar value data, such as banks and telecommunication companies.
Why should your business measure against Essential Eight?
Essentially, Essential Eight is all about Cyber Security and can be seen as a baseline for businesses to measure their maturity against, but it should be just one part of a wider framework that you should have in place. Cyber threats are constantly evolving, so businesses need to adapt to disruptions caused by Cyber Security incidents so that they can maintain business operations. This includes detecting, managing and recovering from incidents. We have other articles on our blog relating to these, so please read those to understand what your business should be doing to protect itself.
By measuring your business against the framework, your business can increase its knowledge of Cyber Security in business and identify company risks and how to control them. It allows your business to create a roadmap going forward that you can tick off to know that your company is becoming secure, and it gives you something to assess your service provider with to ensure they are integrating the Cyber Security processes within your business.

Limitations of Essential Eight
As mentioned, Essential Eight should not be used in isolation to protect your organisation. It’s not a fully-fledged Cyber Security framework and will not protect you from ever having cyber threats. For example, if you’re at Maturity level Three, this will not stop adversaries with the time, money and effort to compromise your business.
The Essential Eight is currently just a loose framework for your business to get started with implementing Cyber Security strategies to protect your businesses. When data leaks can cause your business to be in breach of laws such as The Privacy Act, you need to ensure that you are adequately covered.
The framework is also primarily designed for Microsoft Windows-based businesses, which represent the majority of public sector organisations’ corporate environments, hence why it was introduced by the government. So, while it’s not specifically designed for other operating systems like Mac, Cloud, Operational Technology (OT) or Linux, you can still use it to support your organisation’s Cyber Security development.
So, what are the Essential Eight strategies?
The Essential Eight strategies are designed to address the most common types of cyberattacks that businesses face. They are practical, actionable and cost-effective. Here’s a brief overview of each of the Essential Eight strategies:
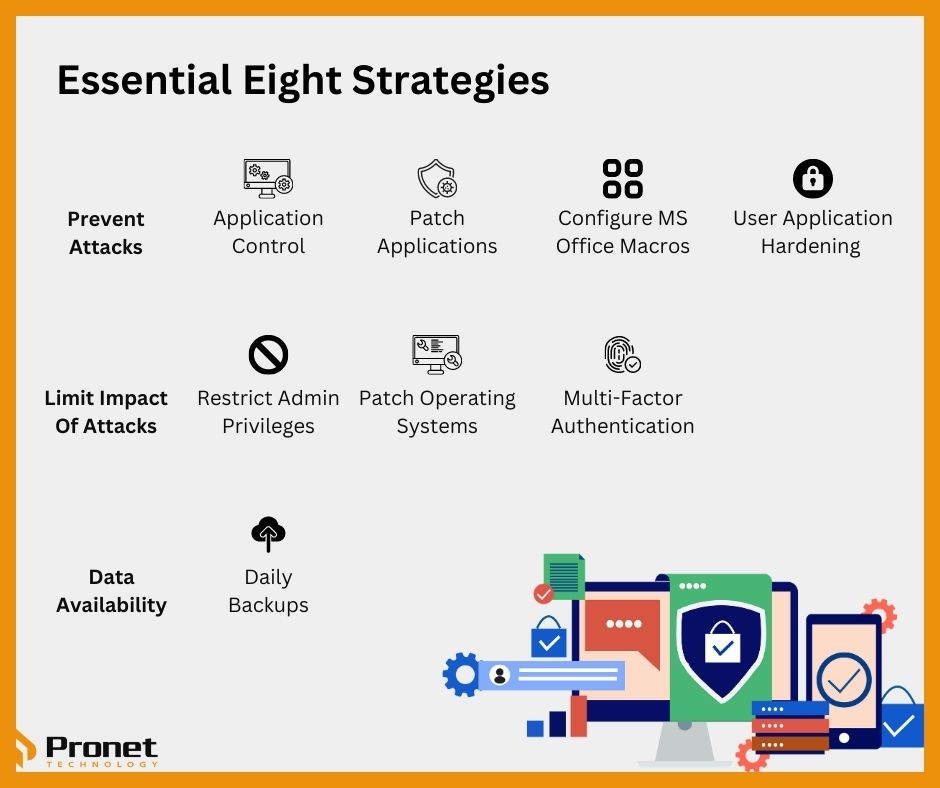
- Application control: This strategy involves creating a list of approved applications that can be executed on a system. By doing this, organisations can prevent malicious software from running on their systems.
- Patch applications: Regularly patching applications can help businesses fix vulnerabilities in their software. This reduces the likelihood of cyberattacks that exploit these vulnerabilities.
- Configure Microsoft Office macro settings: Cybercriminals often use Microsoft Office macros to deliver malware. Configuring the macro settings in Microsoft Office can help SMEs prevent this type of attack.
- User application hardening: Blocks or removes common software used to download or run malicious software and prevents malicious software from running on business’ networks.
- Restrict administrative privileges: Limiting administrative privileges can help businesses prevent malicious actors from gaining access to critical systems.
- Patch operating systems: Similarly, regularly patching operating systems can help organizations fix vulnerabilities in the underlying software. This reduces the likelihood of cyberattacks that exploit these vulnerabilities.
- Multi-factor authentication: Using multi-factor authentication can help organisations prevent unauthorised access to their systems. It involves requiring two or more forms of authentication before granting access.
- Daily backups: Regularly backing up data can help businesses recover from cyberattacks. In the event of a ransomware attack, for example, businesses can restore their data from a backup rather than paying the ransom.
While you might not understand the technical processes of each of the Essential Eight, your IT service provider should be implementing these strategies to help your organisation protect itself against cyber threats. Talk with your MSP to see how and if they’re implementing these into your business.
Does my business need to implement Essential Eight?
While it is not mandated to do so, the framework is highly recommended by the government for Australian businesses to follow. At Pronet Technology, we recommend your company start integrating the framework as soon as possible. Even though we’re an MSP, over the last five so years, we’ve been doing all we can to learn more about and specialise in Cyber Security as we believe it plays an integral role in the longevity of businesses.
While ACSC recommends all businesses be at maturity level 3, each organisation’s Cyber Security level depends on its business need, size and complexity. As a business, conduct a risk assessment alongside your IT service provider to determine, analyse and prioritise the gaps in your business that can be strengthened and then act on those.
There are always going to be some challenges to improving Cyber Security within your business. It could be that you lack the staff and funding or that you don’t have the knowledge to successfully implement Cyber Security. You could have other organisational priorities or believe ad-hoc security is enough. Some people in the business might not yet be on board or you just don’t know how to improve. Cyber Security runs throughout the business so it’s something that everyone needs to understand and come on board with.
Most companies these days outsource their IT systems to service providers. Make sure you know the cyber maturity of your MSP in relation to Essential Eight so that you can build a strong working relationship with the MSP to ensure your business is protected.
By implementing these strategies, SMEs can significantly reduce their risk of cyberattacks. Essential Eight is not a silver bullet, but it’s a great starting point for any organisation looking to improve its Cyber Security posture. It’s important to note that Cyber Security is an ongoing process, and businesses should continually assess and improve their security measures.



