Does Essential Eight Impact my Business?

As a business owner or IT professional, you may have heard about Essential Eight, a set of Cyber Security strategies introduced by the Australian Cyber Security Centre (ACSC) to help organisations protect themselves against cyberattacks. But you might be wondering, does the government’s recommendation of implementing Essential Eight affect my business? In this blog post, we will explore what Essential Eight is and whether it is relevant to your business.
What is Essential Eight?
Essential Eight is a set of eight Cyber Security strategies that the ACSC has identified as essential for organisations to protect themselves against cyberattacks. It was developed to help companies comply with Cyber Security laws, legislations and regulations. The strategies cover a range of security controls that should be implemented to mitigate against the most common cyber threats. Essential Eight is not a prescriptive set of rules, but rather a framework that organisations can use to identify and prioritise their security needs.
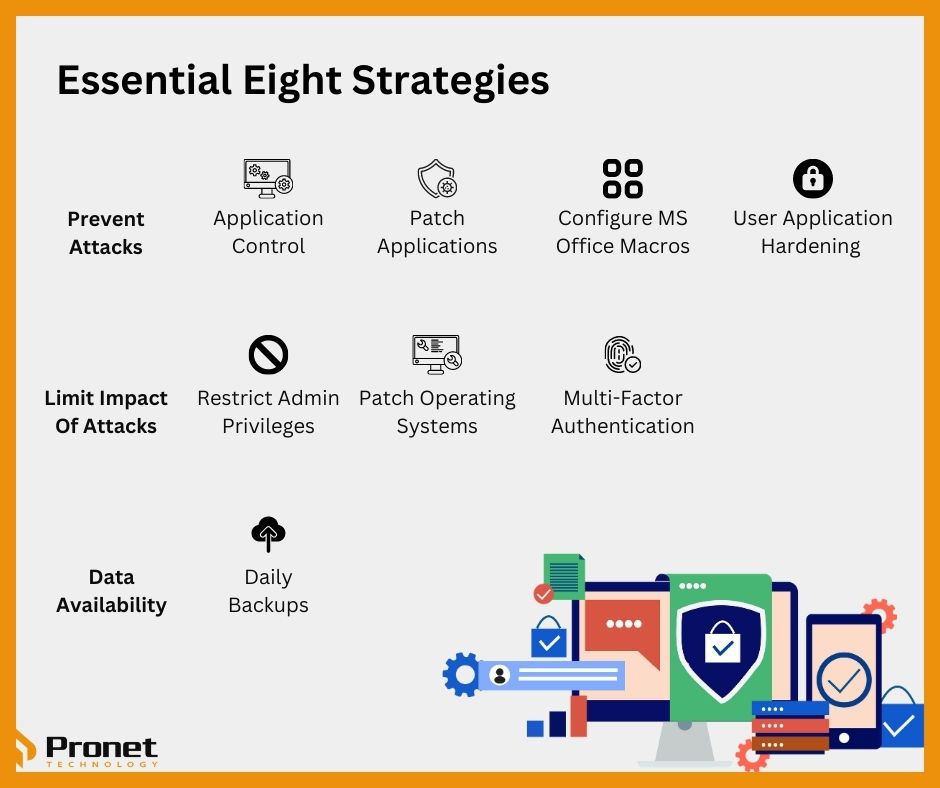
The eight strategies are:
- Application control
- Patching applications
- Configure Microsoft Office macro settings
- User application hardening
- Restricting administrative privileges
- Patch operating systems
- Multi-factor authentication
- Daily backups
Each strategy is designed to address a different aspect of Cyber Security and should be implemented according to the specific needs of your organisation.
By assessing your business against Essential Eight, your compliance with the strategies is measured in terms of its ‘Maturity Level,’ which ranges from zero to three.
Will Essential Eight impact my business?
Currently, Essential Eight is simply recommended guidelines for businesses to measure their Cyber Security maturity against and to give them steps to take to improve their position. We believe this recommendation will soon turn into a mandate, hence why it is something we push our new clients to adopt when we begin working with them. As an MSP that specialises in Cyber Security, these types of strategies are ones we implement anyway, but since they are now strongly recommended by the government, we try to show our clients, and any potential clients, the importance of seriously taking the time to invest in Cyber Security and to educate their staff about security methods.
For now, will Essential Eight affect your business? The short answer is yes. Even though it is only recommended, it’s recommended for a reason. With harsh penalties for businesses that fall victim to cyberattacks, it would be illogical not to start bringing Cyber Security measures into your company. The framework is centred around preventing attacks, limiting the impact of attacks and data availability, which are issues all businesses should be concerned about.
Insurance companies are now starting to mandate certain security measures, which are part of the Essential Eight, and without these measures, your insurance company will not pay you when a claim is made. Or, the insurance company will not renew your Cyber Security coverage. What we also notice is that many small businesses fill out their insurance questionnaire without consulting the right IT people, which often leads to incorrectly stated responses to some of the Cyber Security questions. In cases like these, while a Cyber Security policy is taken out, in the unfortunate event when the small business is attacked and compromised, the insurance company will not honour the covers.
Implementing Essential Eight will require time and resources from your organisation, however, the long-term benefits of implementing these strategies can far outweigh the initial investment.

By implementing Essential Eight, you can:
- Improve your Cyber Security posture: Implementing the Essential Eight can help improve your organisation’s Cyber Security posture, making it more difficult for cybercriminals to breach your network.
- Reduce the likelihood of a data breach: The Essential Eight strategies are designed to protect against the most common cyber threats, reducing the likelihood of a successful attack.
- Save money in the long run: The cost of a data breach can be significant, both in terms of financial costs and damage to your organisation’s reputation. By implementing Essential Eight, you can reduce the likelihood of a data breach, potentially saving your organisation significant costs in the long run.
- Privileged Access Management (PAM): By implementing Essential Eight, you thereby place administrative restrictions on applications, operating systems and devices on a user-by-user basis which allows for increased data security, increased control over operations, reduced risks stemming from human error, reduced cost due no more over expenditure on materials and resources and greater insight into how applications, systems and devices are used.
- Meet compliance requirements: Many regulatory requirements, such as the Australian Privacy Act 1988, require organisations to implement reasonable measures to protect personal information. Implementing Essential Eight can help your organisation meet these compliance requirements.
Challenges to implementing Essential Eight
While implementing Essential Eight can provide significant benefits, it is not without its challenges. Some of these include:
- Lack of resources: Implementing Essential Eight can require significant time and resources, which can be a challenge for small and medium-sized organisations.
- Complexity: Some of the Essential Eight strategies, such as application whitelisting and multi-factor authentication, can be complex to implement and manage.
- Resistance to change: Introducing new security measures can sometimes be met with resistance from employees who may see the measures as an inconvenience.
- Lack of understanding: Some organisations may not fully understand the risks posed by cyber threats and may not see the need for implementing Essential Eight.
Essential Eight is a set of Cyber Security strategies designed to help organisations protect themselves against cyberattacks. While implementing Essential Eight can require time and resources, the long-term benefits of improved Cyber Security posture and reduced likelihood of data breaches can far outweigh the initial investment. By implementing Essential Eight, businesses can better protect themselves against the most common cyber threats and meet regulatory compliance requirements. However, challenges such as lack of resources, complexity, resistance to change and lack of understanding can make implementing Essential Eight a challenge for some organisations.



